
Attack Surface Monitoring (ASM)
Vulnerability Management

Breach and Attack Simulation (BAS)
Automated Red Teaming
EDR, SIEM, SOAR, Deception, AMTD, UEBA
CNAPP - CSPM, CWP, CIEM, Cloud ASM
Container Security
Automated Moving Target Defense (AMTD)
Network Deception
NAC
NDR
CPS Protection
OT IDS
Zero-Trust Access
OT Firewall
GRC Management
GRC Engineering
AI-Powered Risk Management


No integration headaches. One pane of glass. Single security data format. One platform.
Analyze and validate your infrastructure and security using adversarial thinking. Fix everything – from errors to exposures.
Minimize blast radius by stopping threat actors in their tracks. Strengthen security with pre-emptive guidance and cross-domain threat coverage.




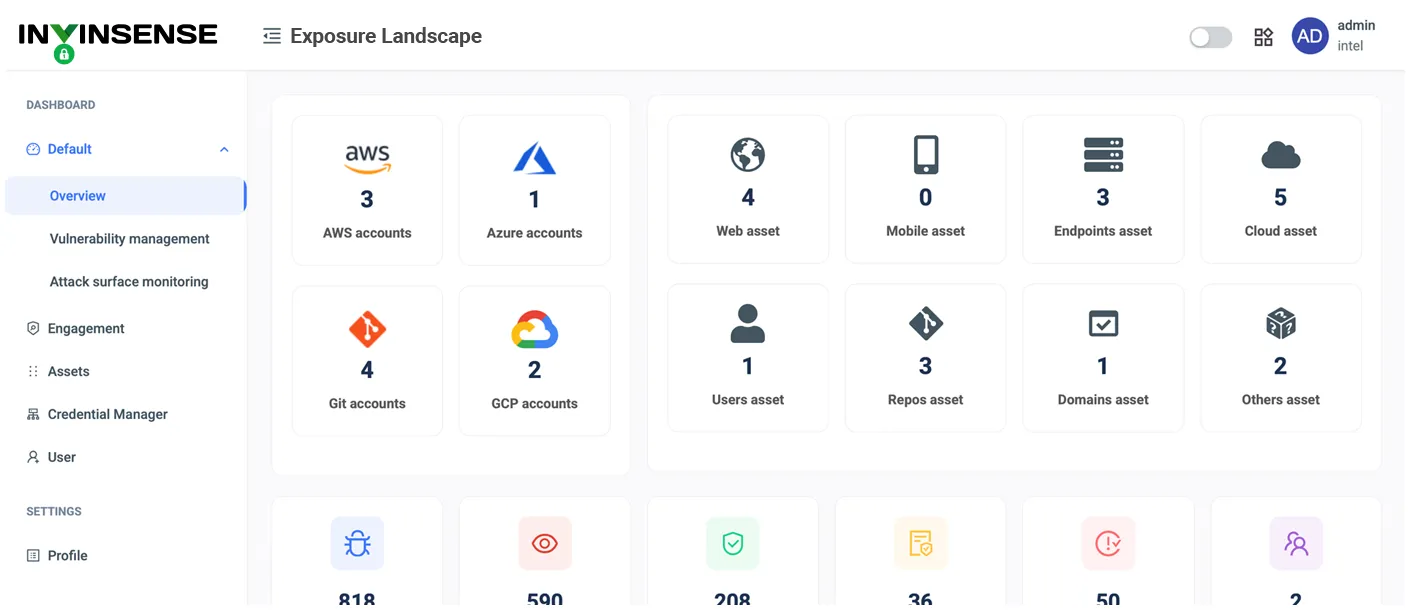
Continuously scans your organization’s digital environment, including data on the surface web as well as the dark web, to identify potential vulnerabilities and exposures. By mapping out all the assets, including networks, applications, and devices, it provides a comprehensive view of the potential entry points, which attackers might exploit.
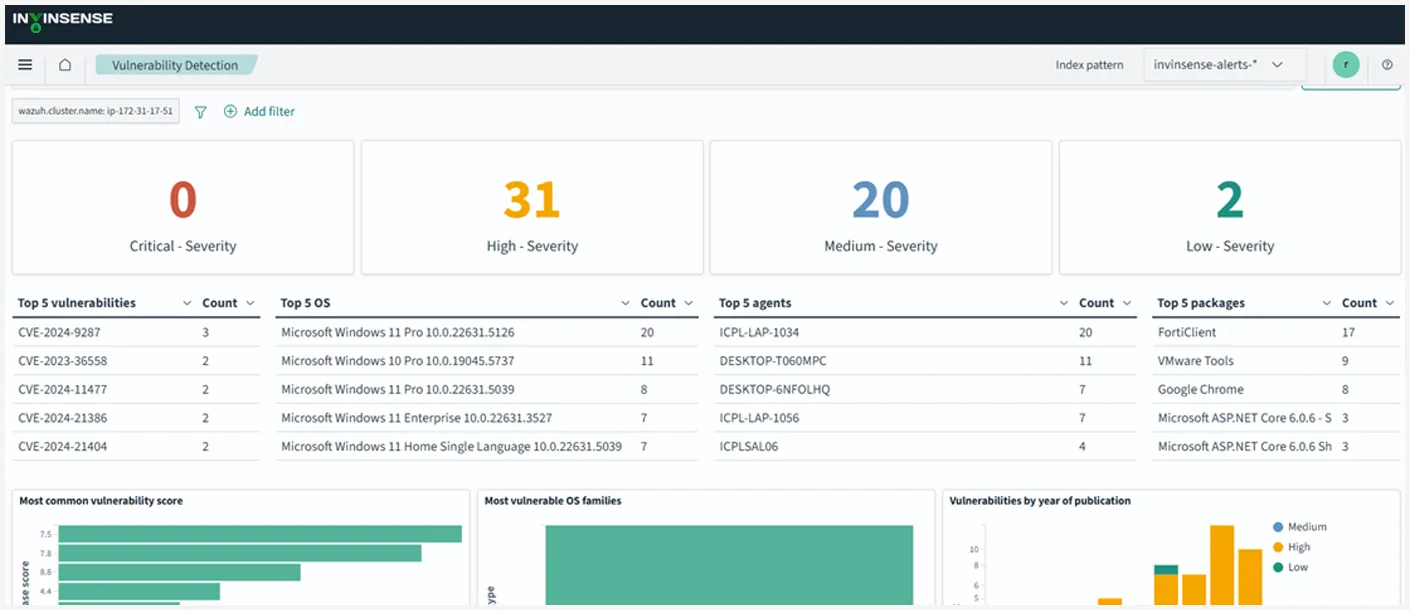
The module consolidates DevSecOps, security orchestration and full lifecycle vulnerability management capabilities. It helps ingest vulnerability and threat exposure information from a variety of sources, enablinga centralised vulnerability management and exposure assessment solution that gathers, stores and analyses thousands of vulnerabilities in one place. Additionally, the module also allows managing application security program, maintain productand application information, triage vulnerabilities and push findings to popular enterprise service management and workflow automation systems such as JIRA and Slack.

The module provides a sophisticated offensive technology to safely perform adversary emulation and simulate a wide range of cyberattacks. In addition to mimicking attacker behaviour, the technology deeply analyses various attack surface components/cyber assets, security controls and configurations to stress-test the entire infrastructure with a holistic “inside-out” approach. The module is based on MITRE ATT&CK™ framework, and it enables practitioners to achieve its real-world application by replicating the tactics, techniques, and procedures (TTPs) used by Advanced Persistent Threats (APTs) and modern threat actors.

A powerful component in the offensive security arsenal that is also a part of modern adversaries’ playbooks! Provides a highly advanced, cross-platform red teaming tech that helps assess security infrastructure using various evasive and C2 like tactics. The technology also incorporates MITRE ATT&CK mappings into the standard workflow, enabling red teaming operations to understand the coverage of various commands issued in an operation. The module facilitates a plug-n-play architecture where new agents, reverse shellattacks, communication channels, and modifications can be configured on the fly.
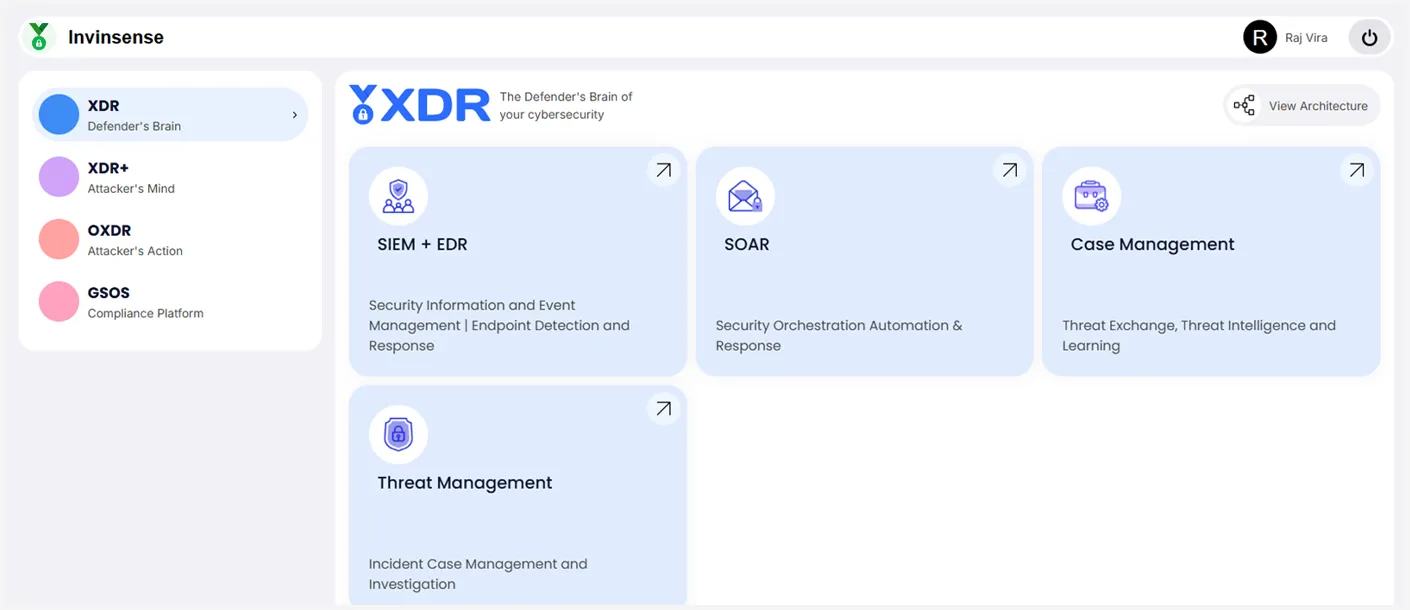
Invinsense Extended Detection and Response (XDR) integrates SIEM, SOAR, EDR, Case Management, Threat Intelligence, and Threat Exchange solutions, making it the most comprehensive XDR offering in the market. These solutions share vital security data through Invinsense security data lake, hence collectively functioning as the “Defender’s Brain” in cybersecurity defence.
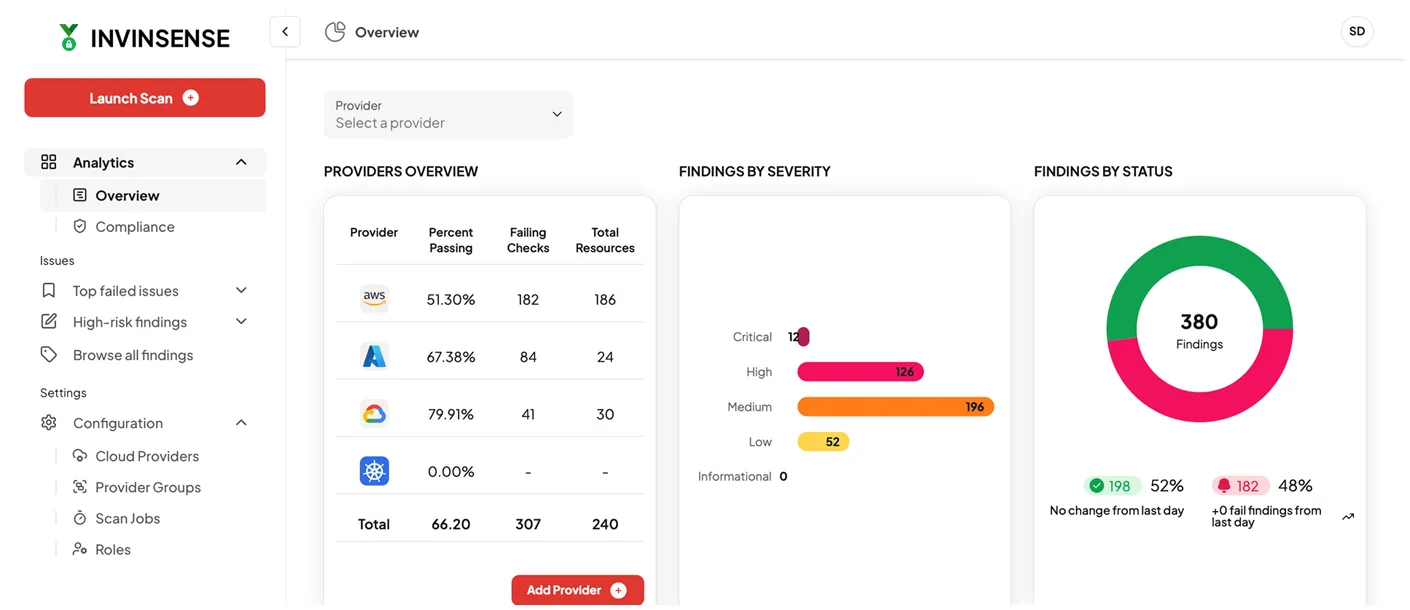
By combining Application Security Posture Management (ASPM) and Cloud Native Application Protection Platform (CNAPP) capabilities, Invinsense uncomplicates security, enables a comprehensive app sec view across the entire cloud and digital infrastructure and helps achieves streamlined remediation with a holistic view of risk and improved security visibility across SDLC. The module combines various key components such as CSPM, CIEM, CWPP, Identity Security, SAST, DAST, SCA, SBOM, API security and Infrastructure-as-Code (IaC) security.

The module combines advanced deception and Automated Moving Target Defense (AMTD) capabilities to keep evolving adversaries at bay. This is done by dynamically detecting lateral movement, sophisticated network penetration and other evasive techniques, ensuring an organization's crown jewels are hidden, protected and remain uncompromised. Invinsense’ AMTD is a high-accuracy and innovative technology recognized by Gartner for enabling a shift from an ineffective “detect and respond” model to a "pre-emptive defense” approach. It capably complicates modern attackers’ and ransomware actors’ tactics to exploit the ever-expanding attack surface, discover and target vulnerabilities within the enterprise network.

Result of a successful research productization, Invinsense OT and IoT security module provides a specialized cybersecurity capability, which is designed to safeguard industrial and critical infrastructure systems by continuously monitoring and detecting intrusions that are specifically targeted at OT and IoT landscapes. The technology plays a crucial role in maintaining the reliability and security of essential operations in sectors such as power & utility, oil & energy, manufacturing, automobiles, pharmaceuticals and transportation.
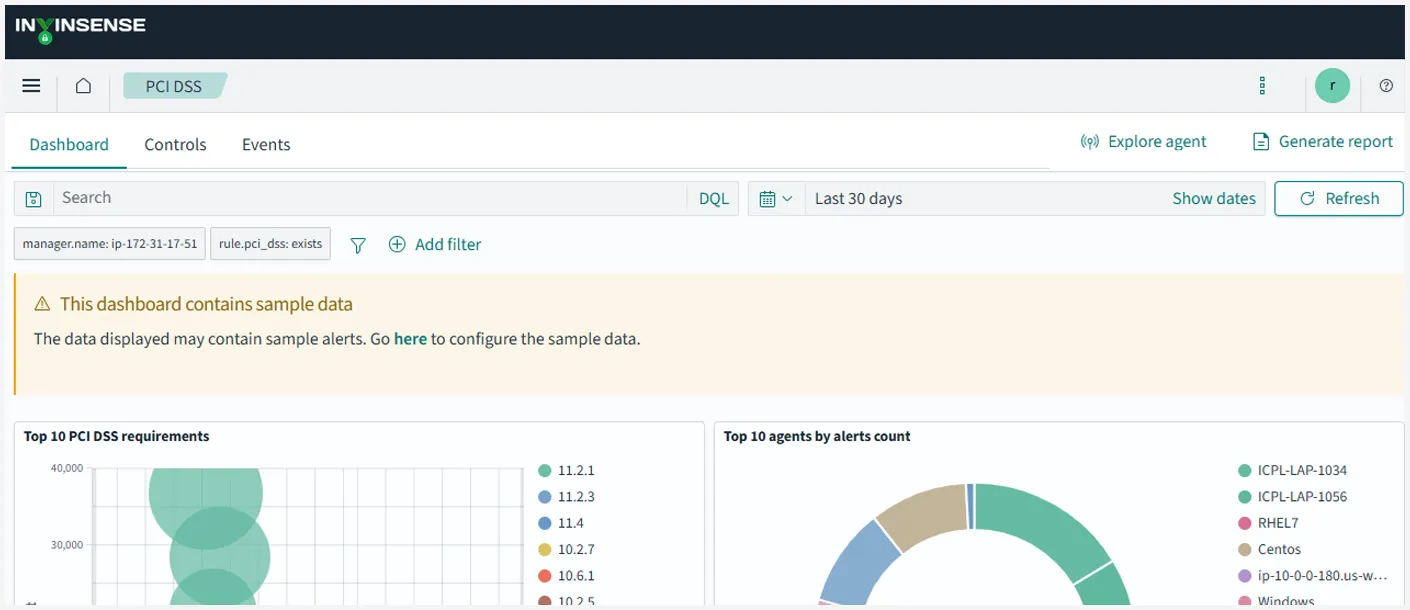
The module provides an intuitive solution for managing governance, risk and compliance (GRC) concerns and tasks. A wide range of built-in and pre-defined templates enable security teams to create policy documents and simulated test exercises on the fly, while letting them streamline workflows with consistency and accuracy. It assists in creating acybersecurity strategy, streamlining compliance management, enhancing security posture, reducing risks, increasing cybersecurity awareness and preparedness, and enabling organizations to meet regulatory requirements and safeguard sensitive & regulatory compliant data.
Discover complete cybersecurity expertise you can trust and prove you made the right choice!
